AI-driven incident response is rapidly becoming the backbone of modern enterprise cybersecurity. As cyber threats grow more automated, sophisticated, and persistent, traditional manual response models can no longer keep pace. In 2026, organizations face a reality where security incidents are not exceptions, they are constants. From ransomware campaigns to identity-based attacks and cloud misconfigurations, the […]
Category: Cybersecurity
Cyber-Resilient Data: How NetApp Is Enabling Enterprise Security
Cyber-resilient data has become a critical priority for enterprises as artificial intelligence and cloud systems increasingly drive business operations. In 2026, organizations are no longer asking whether to use digital platforms, they are asking how to protect data, recover from attacks, and maintain operational continuity. Cyber threats have become one of the most serious risks […]
Deepfake Fraud: How AI Is Changing Cybercrime Forever
Deepfake technology was once seen as entertainment. Today, it has become one of the most dangerous tools in modern cybercrime. Deepfake fraud is now being used to impersonate executives, manipulate video calls, and commit financial scams that are almost impossible to detect with the human eye. As artificial intelligence becomes more accessible, cybercriminals are no […]
What is Identity and Access Management & Why This Is Now a CEO-Level Priority in the Cloud Era
In today’s hyper-connected world, every business relies on digital systems to operate, innovate, and grow. But as companies shift to the cloud, one challenge has quietly become the backbone of security, compliance, and trust: Identity and Access Management (IAM). Before we explore why leaders are elevating IAM cloud strategy to the CEO’s desk, it’s important […]
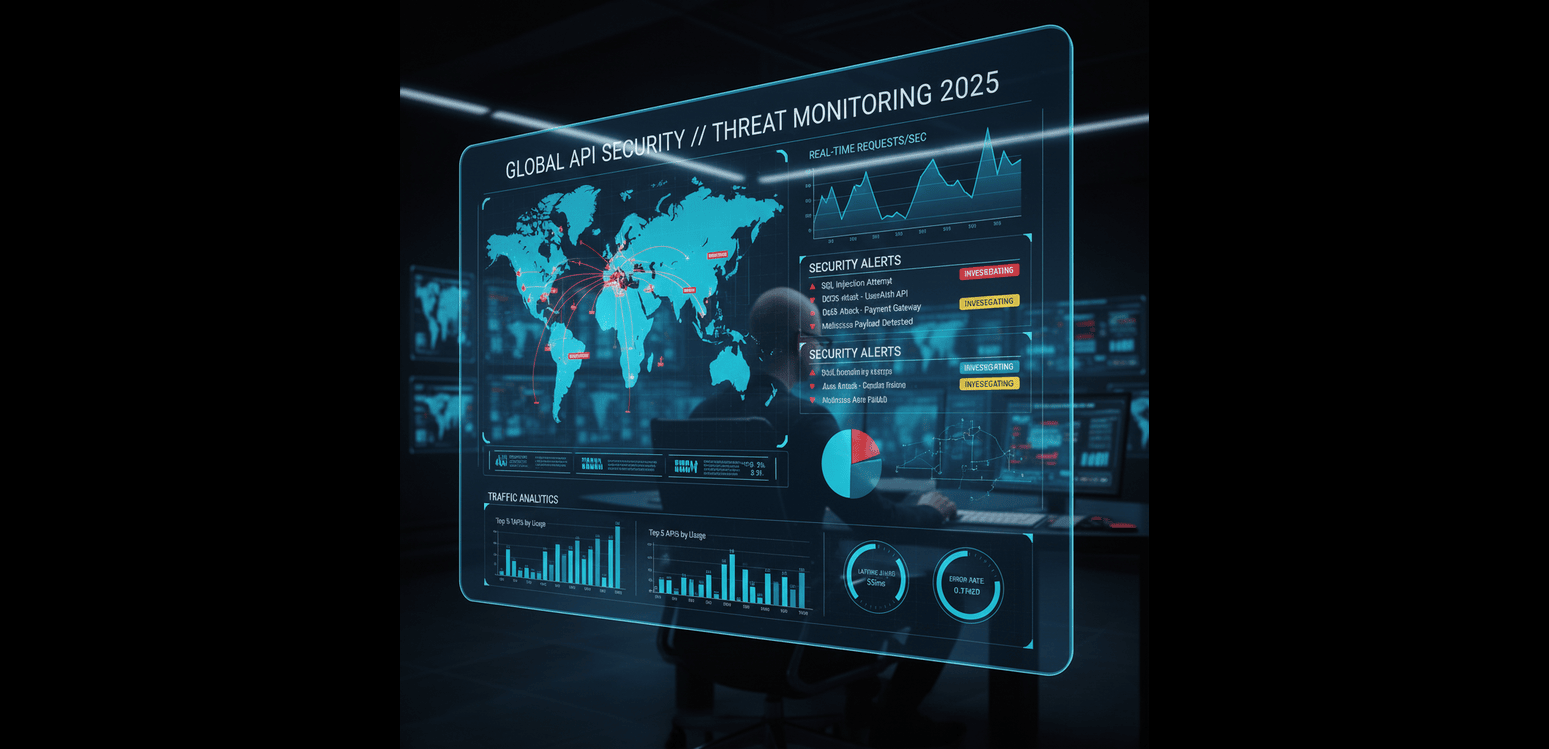
Why API Security 2025 Matters More Than Ever
APIs have become the backbone of digital business, powering mobile apps, cloud platforms, integrations, and almost every modern software experience. As companies scale their digital ecosystems, attackers are shifting their focus to the most exposed entry point APIs. This is exactly why API security 2025 matters more than ever. Whether you’re managing financial platforms, SaaS […]
Sophos 2025: How AI-Powered Cybersecurity Is Redefining Business Protection
In 2025, AI-powered cybersecurity has become the backbone of digital defense. With new attack surfaces emerging across cloud, IoT, and hybrid workplaces, businesses can no longer rely on manual response systems. Among the global cybersecurity innovators, Sophos stands out for transforming how enterprises predict, prevent, and respond to threats not reactively, but intelligently and autonomously. […]
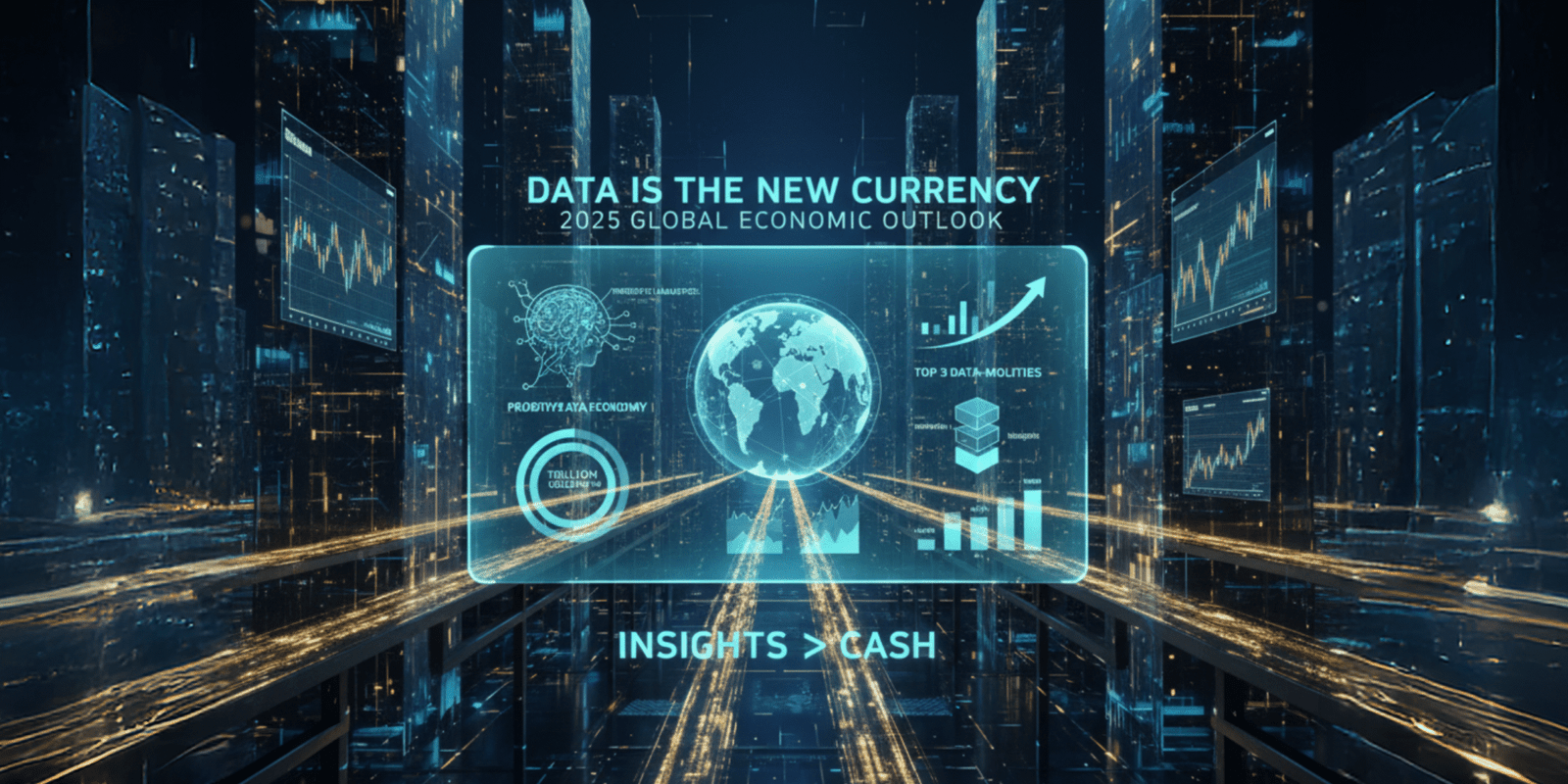
Data Is the New Currency: Turning Insights Into Business Growth
In 2025, organizations no longer compete only on innovation or price — they compete on data intelligence. Data is the new currency driving business transformation across every sector. From digital platforms to manufacturing floors, every click, swipe, and transaction generates insights that define how businesses compete, innovate, and grow. But owning data is no longer […]
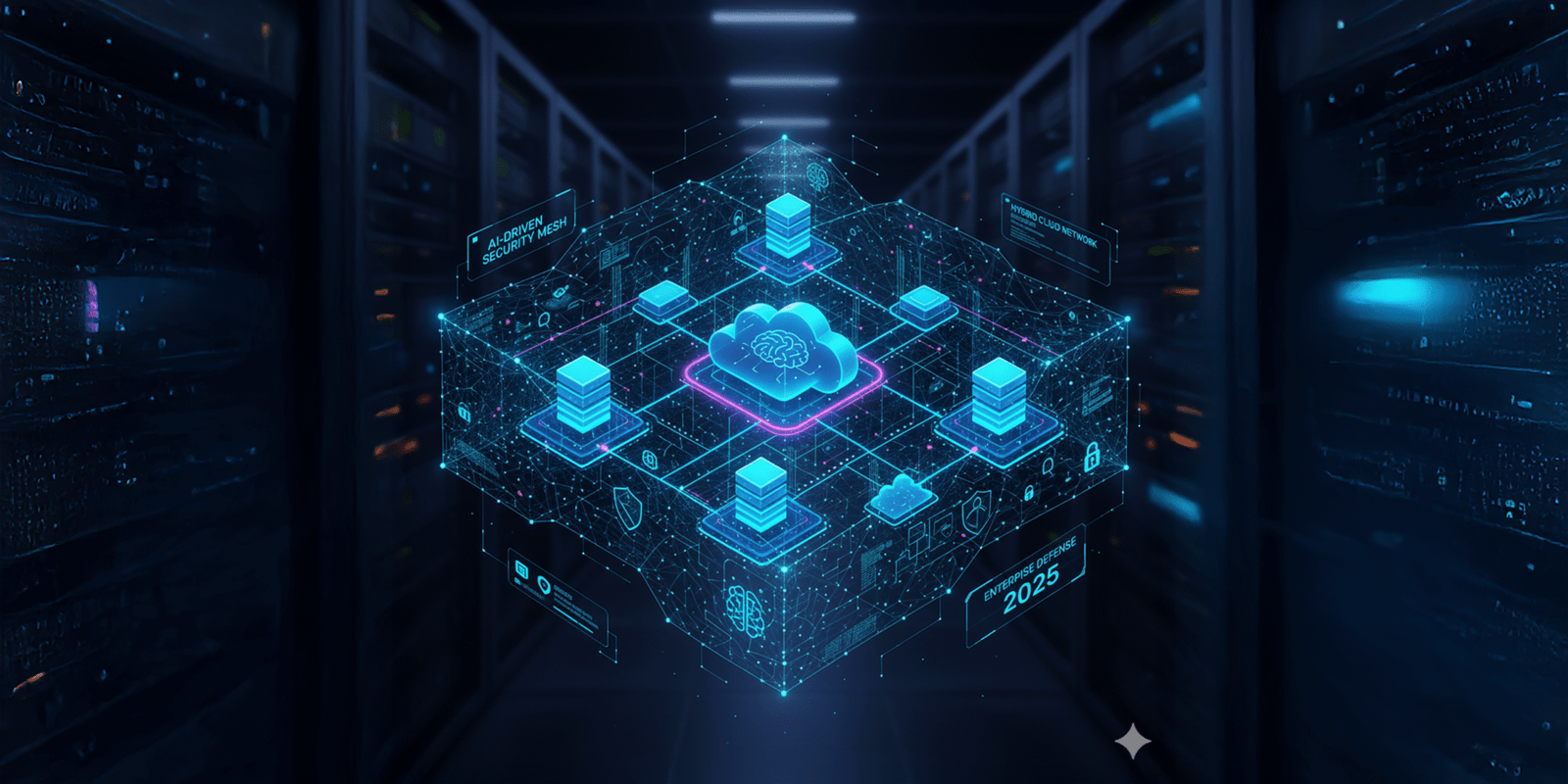
Cloud Security Mesh 2025 & Hybrid Software Reality
Cloud Security Mesh 2025 has become a defining shift in enterprise security and IT scalability. As companies adopt hybrid infrastructure and multi-cloud ecosystems, they need solutions that unify protection across every system. The mesh model delivers exactly that — a dynamic and connected security framework built for distributed environments. Why Cloud Security Mesh 2025 Matters […]
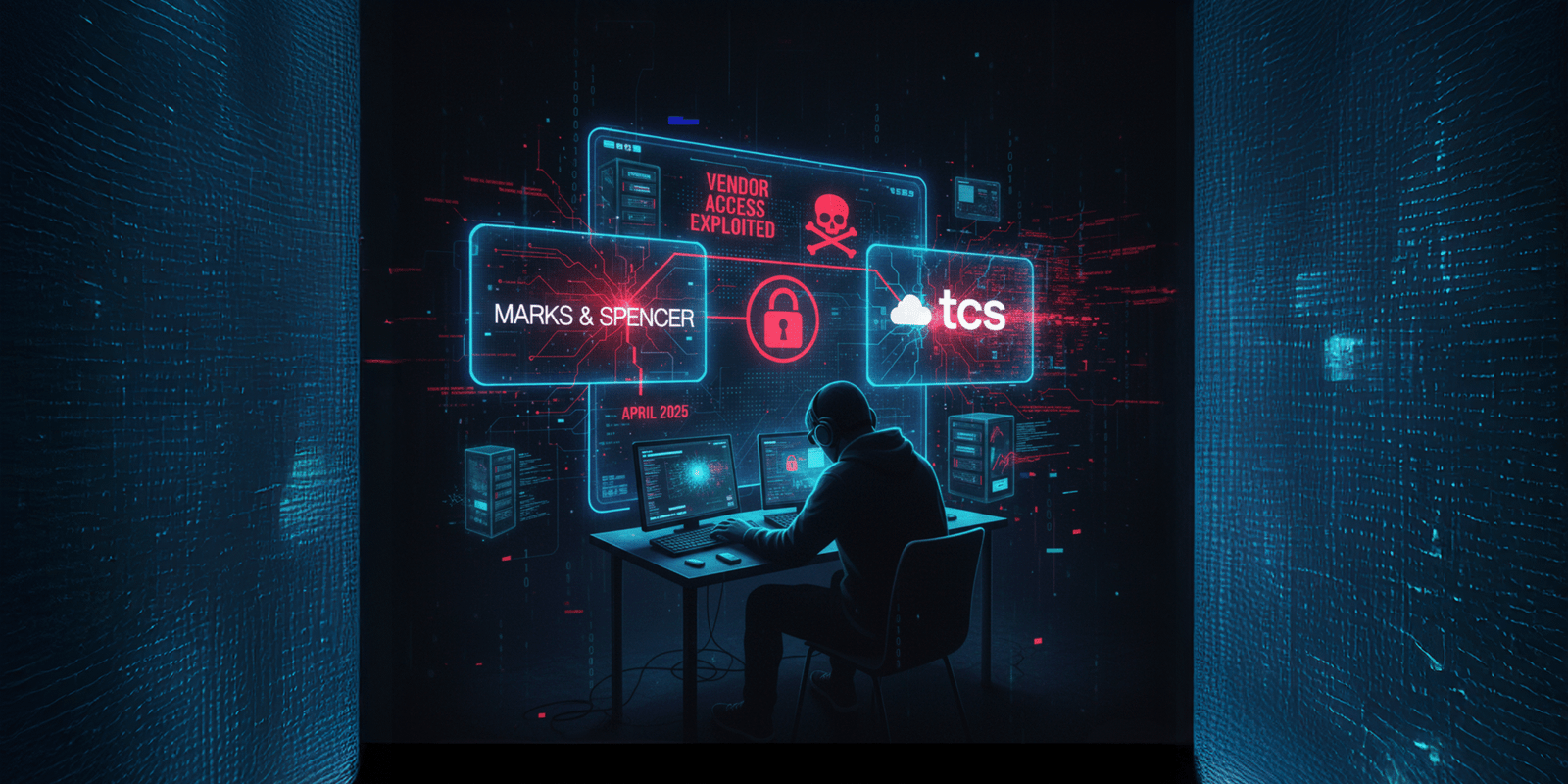
M&S Cyber Attack 2025: A Wake-Up Call for Tech & HRTech Vendors
The M&S cyber attack 2025 shows how a major retailer’s trusted IT system collapsed due to a third-party access point. For tech firms and HRTech vendors, the lesson is clear: weak vendor controls, easy help-desk access, and social engineering still create the biggest exposure. When outsourcing partners hold keys to your systems, their gaps become […]
AI Meets Cybersecurity: India’s 2025 R&D Push
AI Meets Cybersecurity: India’s 2025 R&D Push marks a defining moment in India’s digital defense story. In October 2025, the National Institute of Electronics & Information Technology (NIELIT) and the Future Crime Research Foundation (FCRF) joined forces to strengthen cybersecurity through AI and digital forensics. This groundbreaking partnership clearly reflects India’s determination to create a […]